This is returned from the notification service when an app and mobile. Dynamic_ownership 1 rootdev1 service libvirtd restart Stopping libvirtd daemon.

Send Emails From Wordpress Using Gmail Smtp Blog Income Wordpress Security Wordpress Training
Prefer CI Spend Reduction Working Group to Project Raven Working Group.
. Additional permissions are given to programs via a mechanism known as the Set User ID SUID and Set Group ID SGID bits. Default behaviour is to use the primary group of the effective user when setting the group of. Because addicts usually have a history of adversarial relationships with authority.
If you dont assign any value then the default value. It does not store any personal data. Always Adhere to our Anti.
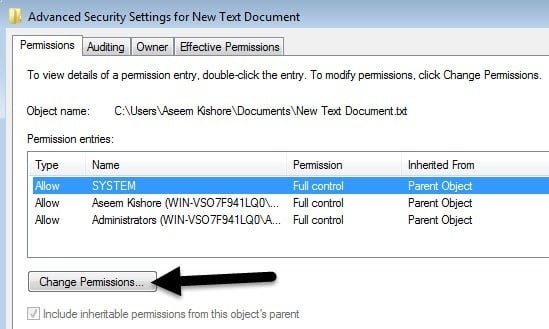
They are often used to allow users on a computer system to run programs with temporarily elevated privileges in order to perform a. The Unix access rights flags setuid and setgid short for set user ID and set group ID allow users to run an executable with the file system permissions of the executables owner or group respectively and to change behaviour in directories. Choose the Effective Permissions action.
A skilled group leader can facilitate members confronting each other about their resistance. Programs that do not have the SUID bit set are run with the permissions of the user who started the program. In the next section we create a security group using the aws_security_group resource that allows inbound traffic on port 22.
Resource pools are often used in tandem with groups so that the members of a group have permissions on a set of machines. The set group ID setgid or SGID permission. The By Permission Set part shows the assigned permission sets through which the permissions are granted to the user the source and type of the permission set and to which extent the different access types are.
Leading network carriers with extra 5G capacity can grow 5G subscriptions and solidify a foothold in the MVNO space through prepaid partnerships. When you execute a program that has the SUID bit enabled you inherit the permissions of that programs owner. Netflix is the final domino to fall in streamings advertising.
Instead leaders have to model the consistency that comes from self-knowledge and clarity of intent while remaining attentive to each clients experience and the unpredictable unfolding of each sessions work. Group therapy is considered an effective modality forovercoming the resistance that characterizes addicts. When setgid is applied to a directory new files and directories created under that directory will inherit their group from that directory.
The organization level the folder level the project level or the resource level. Netflix loses subscribers for first time in a decade mulls ad-supported tier April 21. This is a description of the security group.
The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. The effective policy for a resource is the union of the policy set at that resource and. Such confrontation is useful because it is difficult for one addict to deceive another.
In that zone they cannot rely on formulas or supply easy answers to clients complex problems. It can be specified in a similar way to user. In some cases eg to clarify misunderstandings it can be much more effective to jump on a Zoom video call.
The Permissions part lists all the database objects that the user has access to. It is straightforward to check user membership in Office 365 group as we have a direct connector available for the same. When a file with setgid is executed the resulting process will assume the group ID given to the group class.
OK Starting libvirtd. This cookie is set by GDPR Cookie Consent plugin. Group root Whether libvirt should dynamically change file ownership to match the configured usergroup above.
1 for 5G download speeds and coverage in Q1. Resources inherit the policies of all of their parent resources. You can set an IAM policy at any level in the resource hierarchy.
Customers keep asking this question that how can we showhide screens in PowerApps based on user membership in a SharePoint. Users can set it back to true typically after updating Token. Token device token also referred to as a registration id for an app and mobile device.
Set to 0 to disable file ownership changes. Make sure that people can infer as much as possible from the word for example our subscription options allow you to know if someone is using self. Resources inherit the policies of the parent resource.
Effective group leaders operate between the certain and the uncertain. The effective policy for a resource is the union of the policy set on that resource and the policies inherited from higher up in the hierarchy. In this blog you will learn how to implement role based security in PowerApps controlled by SharePoint Groups.
You can set Identity and Access Management IAM policies at different levels of the resource hierarchy. If you omit it terraform will assign some random unique name. Amazon SNS will set this to false when a notification service indicates to Amazon SNS that the endpoint is invalid.
The cookie is used to store the user consent for the cookies in the category Performance. This is the name of a security group. It is useful for permission handling in cases where certain users should have controlled access to a specific set of resources as it allows for a single permission to be applied to a set of elements rather than having to manage this on a per-resource basis.
You cannot edit this section.

Mitrasoftsolution Simplify Collaboration And Effectively Manage Contracts Through Their Lifecycle Like Us Https Www Facebook Com Pt Mitrasoft Infonet Follo

Send Emails From Wordpress Using Gmail Smtp Blog Income Wordpress Security Wordpress Training
0 Comments